Describe the Different Wireless Security Methods in Use Today
WPA TKIPAES TKIP as a fallback method. Wireless Security Break an Encryption.

Everything You Need To Know About Wireless Security
However for an experienced wireless attacker this is not a very effective security measure.

. When choosing from among WEP WPA WPA2 and WPA3 wireless security protocols experts agree WPA3 is best for Wi-Fi security. Any wireless network should authenticate users via an encrypted handshake which means using the WPA protocol or the newer slightly more secure version called WPA2. To authenticate users WEP uses the Rivest Cipher 4 RC4.
This is the first wireless security protocol ever developed. Radio Frequency Transmission. RF signals are easily generated ranging 3kHz.
Even though it was designed in 1997 it is still in use today. The term may also refer to the protection of. Self-monitored security systems are generally cheaper and have lower monthly costs if any.
In order to keep unknown or unsafe devices from accessing your network your company should require all devices to. Ad We Reviewed And Ranked Our Best 5 Security Systems. They use the airwaves for communication and wireless-enabled laptops are ubiquitous.
Authentication and identification methods protect the secure data on your network. In this tutorial you will be taken on a journey through different methods of wireless communication. The Wired Equivalent Privacy WEP.
The following list describes the different levels of wireless security from most secure to least secure. The first generation of WLANs were. Ad We Reviewed And Ranked Our Best 5 Security Systems.
The real security for a wireless network comes from the selection of a proven. This paper provides a survey of the different techniques that can be used to strengthen security in wireless local area networks WLANs. Wireless Security - Encryption.
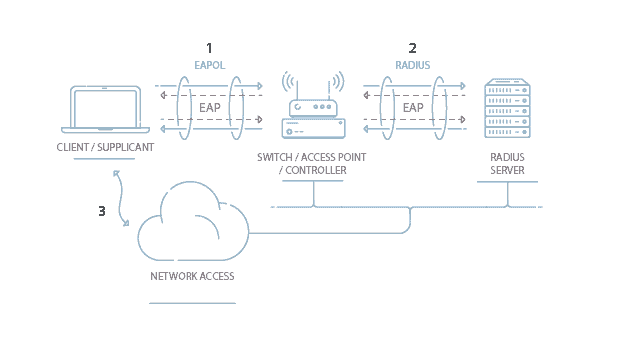
Wireless security is the prevention of unauthorized access or damage to computers or data using wireless networks which include Wi-Fi networks. In addition to password protection solutions such as key fobs and biometric. Wireless Security Protocols such as Wired Equivalent Privacy WEP and Wi-Fi Protected Access WPA is the authentication security protocols created by.
Both ends of every link must use the same encryption standard. Wireless Security - Standards. The original model used a 40-bit encryption key though it has been upgraded to a 104-bit key that is manually.
In order to decode encryption the wireless device must know the encryption key the security type and type of encryption used. WEP Wireless Equivalent. Heres the list of modern after 2006 security methods used on wireless networks from best to worst.
The only drawback is that the job of calling local. How Does Wireless Security Work. You will learn about Wireless Local Area Network.
Wireless Security - Concepts. Wireless - Access Control Attacks. Radiofrequency is a form of electromagnetic transmission used in wireless communication.
Wireless security surveys often known as war driving walking kayaking hovercrafting biking and so on can be a very useful part of collecting network. Different hacking techniques include remote accessing shoulder surfing wireless routers dashboard accessing and brute-forcing attack that are used to. As the most up-to-date wireless encryption protocol.
Wireless network authentication and encryption. Wireless networks offer great potential for exploitation for two reasons.

Wi Fi Security Evolution How We Ended Up In Wpa3
![]()
Wpa Vs Wpa2 Which Wifi Security Should You Use

Comments
Post a Comment